Streamlining Security in Software Development with Snyk
As a Senior DevOps Engineer and Docker Captain, I’m constantly evaluating tools that enhance our security posture throughout the software development lifecycle. One such comprehensive solution is the Snyk platform, which offers robust application security from ideation to deployment. Here are some insights based on my experience and how Snyk can be pivotal in securing your applications.
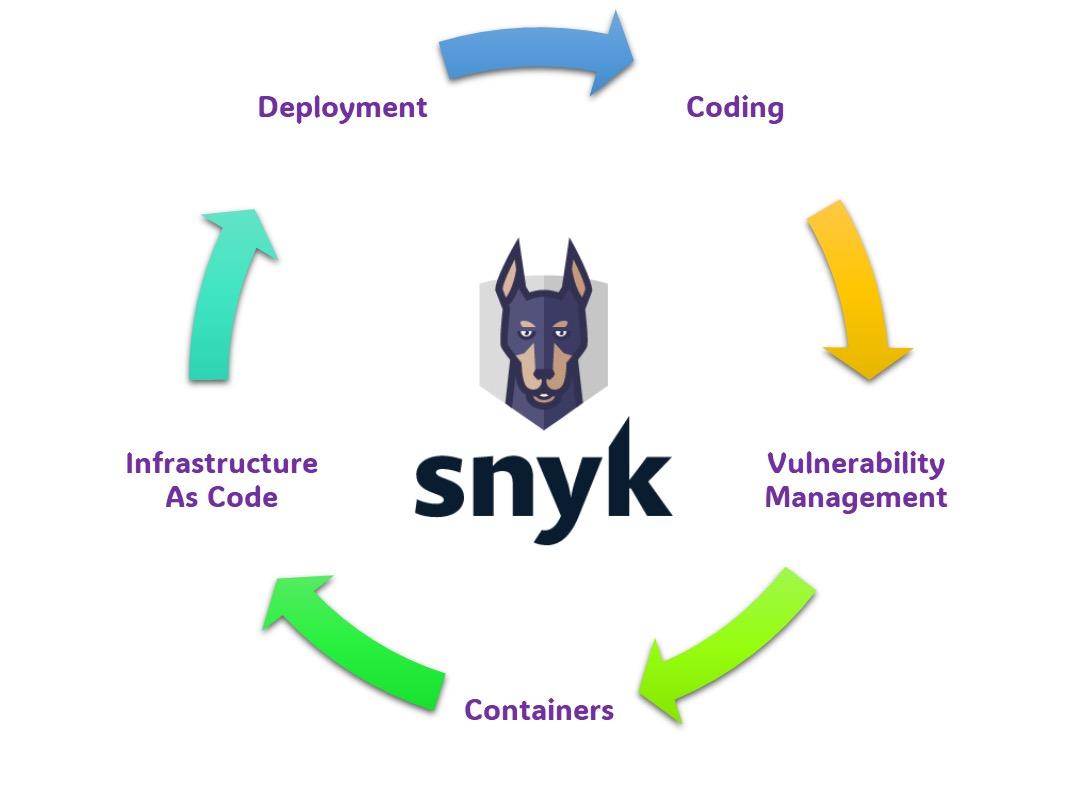
The Continuum of Application Security
Developing an application is inherently a complex process involving multiple stages, each with specific security needs. Yet, the necessity for robust application security remains a constant across all these stages. For instance, secure coding practices are expected right from when the developers start typing out code. Each artifact created or modified during these stages also needs to be secured against potential vulnerabilities.
The challenge arises when enterprises are faced with an array of tools, each catering to different security aspects of the development stages. This not only proves to be costly but also complicates asset management and governance. Moreover, having numerous tools can slow down the build process due to multiple integrations in the build pipeline, causing frustration within the development teams due to the varied interfaces and steep learning curves associated with each tool.
Unified Security with Snyk
Snyk addresses these challenges by providing an integrated platform that spans the entire secure development lifecycle, offering gate controls at each stage. This unified approach simplifies the security architecture, reducing both costs and operational overhead.
Key Features of Snyk in Application Development:
Secure Coding with Snyk Code: As developers integrate Snyk directly into their Integrated Development Environments, they receive real-time feedback on potential vulnerabilities, helping to catch issues early in the coding process. This ‘shift left’ approach ensures that security is embedded from the very beginning.
Vulnerability Risk Management: Modern software development heavily relies on third-party frameworks, which, while beneficial, can introduce vulnerabilities. Snyk scans these open-source packages during the development phase and integrates with code repositories to continuously monitor for new vulnerabilities, enabling timely fixes through pull requests.
Container Security with Snyk Container: Containers, whether used in cloud or on-premises environments, are vulnerable to exploits from insecure code or third-party libraries. Snyk Container helps identify these vulnerabilities early in the development process by integrating with various container repositories and CI/CD pipelines. This feature is crucial for maintaining secure containerized environments.
Infrastructure as Code Security: With the rise of DevOps, misconfigurations in cloud settings have become a significant source of security vulnerabilities. Snyk enhances IaC security by scanning for misconfigurations and enforcing security policies directly within the development tools.
Post-Deployment Monitoring: The responsibility of application security doesn’t end at deployment. Snyk continues to monitor deployed applications, particularly in dynamic environments like Kubernetes, to detect and address new vulnerabilities as they arise. This ongoing vigilance is essential in maintaining the security integrity of applications post-deployment.
In conclusion, Snyk not only consolidates application security into a single platform but also enhances the efficiency and effectiveness of security practices throughout the application development lifecycle. For those interested in integrating these capabilities into their development process, I recommend exploring the extensive documentation provided by Snyk, which offers step-by-step guides on implementing and maximizing the benefits of their tools.
My Services
💼 Take a look at my service catalog and find out how we can make your technological life better. Whether it’s increasing the efficiency of your IT infrastructure, advancing your career, or expanding your technological horizons — I’m here to help you achieve your goals. From DevOps transformations to building gaming computers — let’s make your technology unparalleled!
Refill the Author’s Coffee Supplies
💖 PayPal
🏆 Patreon
💎 GitHub
🥤 BuyMeaCoffee
🍪 Ko-fi
